Cross Site Request Forgery (CSRF)
What is CSRF?
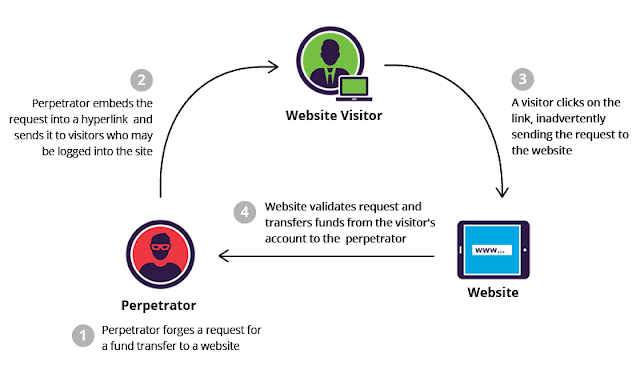
Cross-Site Request Forgery (CSRF) is a type of attack that occurs when a malicious web site, email, blog, instant message, or program causes a user’s web browser to perform an unwanted action on a trusted site for which the user is currently authenticated.
The impact of a successful CSRF attack is limited to the capabilities exposed by the vulnerable application. For example, this attack could result in a transfer of funds, changing a password, or purchasing an item in the user's context with a little help of social engineering (such as sending a link via email or chat).
 |
| CSFR Example |
In effect, CSRF attacks are used by an attacker to make a target system perform a function via the target's browser without knowledge of the target user, at least until the unauthorized transaction has been committed.
If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application.
CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request.
Sites that are more likely to be attacked by CSRF are community websites (social networking, email) or sites that have high dollar value accounts associated with them (banks, stock brokerages, bill pay services).
Methods of CSRF Mitigation
A number of effective methods exist for both prevention and mitigation of CSRF attacks.
From a user’s perspective, prevention is a matter of safeguarding login credentials and denying unauthorized actors access to applications.
Best practices include:
- Logging off web applications when not in use
- Securing usernames and passwords
- Not allowing browsers to remember passwords
- Avoiding simultaneously browsing while logged into an application
For web applications, there are several methods that can be used to protect our own website by generating Cross-Site Request Forgery Tokens in server side and validating them before respond to any client request. They are;
Approaches that do require no server side state:
- Double Submit Cookie Defense
- Encrypted Token Pattern
- Custom Header => e.g., X-Requested-With: XMLHttpRequest
These are listed in order of strength of defense. So use the strongest defense that makes sense in your situation.


Comments
Post a Comment