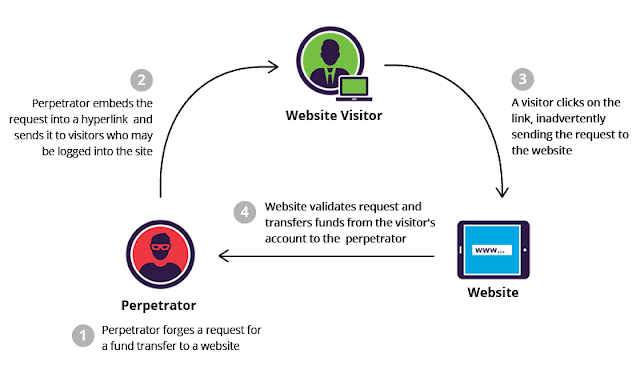
RESTful API

RESTful APIs are application programming interfaces (API) that adhere to architectural style of REST architectural pattern and it is used to HTTP requests to GET, PUT, POST and DELETE data. RESTful API has the following features: Those are the guiding constraints which define a RESTful system. Client–server - The client handles the front end the server handles the backend and can both be replaced independently of each other. Stateless - No client data is stored on the server between requests and session state is stored on the client. Cacheable - Clients can cache response (just like browsers caching static elements of a web page) to improve performance. Uniform Interface - The key to the decoupling client from server is having a uniform interface that allows independent evolution of the application without having the application’s services, or models and actions, tightly coupled to the API layer itself. Layered System - REST APIs have different layers of their a...