How to do a Dictionary Attack using kali Linux
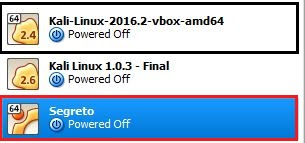
I want to find out login password for Ubuntu operating System. I'm using Kali Linux. Assume that you have a word List and the username to that operating system. Black Boxed - Kali Linux Red Boxed - Ubuntu operating system that I want to log in. 1. Find the mac of the VM. Right click on the VM you want to log in => Click Settings => Click Network => Expand 'Advanced'. You can Find the Mac address of the VM there. Open Kali Linux and run the following commands. 2. Find the IP address of the VM. By looking at the mac address we can find out the IP address. In here it is 3rd IP address which matches the Mac address we have found earlier. IP - 192.168.8.102 3. Find the open ports In here ssh an...