Firewalls
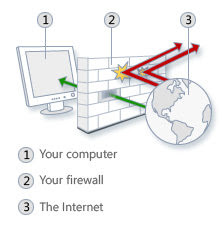
What is a firewall? A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Firewalls have been a first line of defense in network security for over 25 years. A firewall can be hardware, software, or both. Why we need firewall in network? Internet connection leaves you vulnerable to hackers who want to access your financial and personal information. Some hackers may be after your high-speed connection so that they can send malicious viruses and worms, blackening your reputation. Other intruders have the power to destroy your operating system on a whim. A firewall works as a barrier, or a shield, between your computer network and internet. When you are connected to the Internet, you are constantly sending and receiving information. All messages entering or leaving the intranet pass through the firewall, which examines each m...